Transport Layer Security (TLS)
When someone visits your website by entering a common URL starting with http:// their logins and passwords and other confidential data can be intercepted by undesired third parties. Likewise this connection offers no guarantee of authenticity and can be re-directed (or faked) by an ISP or another intermediary. TLS support is not a cure for all things, but it significantly improves:
- confidentiality of data transmission between your web server and the user’s browser
- authenticity for connections your users make with your web server
How TLS/HTTPS works on Deflect
Normally when two computers communicate securely, without a caching proxy service like Deflect, the client (for example a browser) requests the server’s TLS certificate, checks that it trusts the certificate, then encrypts the connection using it. ISPs, businesses and governments – those who own the networks, or any other actor sitting in the middle between the client and the server – cannot look at what’s inside the established communications tunnel.
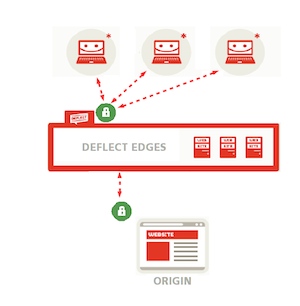
Deflect offers several options for encrypting connections to your website, and can generate TLS certificates or use those that you already possess.
Deflect can generate public-facing TLS certificates through Let’s Encrypt, a certification authority (CA) launched in 2015 and co-founded by the Electronic Frontier Foundation that issues free and easy-to-install certificates with the explicit aim of facilitating and spreading the use of cryptography on the web. Since Let’s Encrypt certificates need to be renewed frequently, Deflect uses longer-lasting origin certificates signed by its own certification authority. Of course, if you already have a TLS certificate, you can use it to encrypt connections between Deflect and your website (origin certificate) as well as between the public and the edges (public-facing certificate), but in the latter case you will need to share your private TLS key with us. If you would rather not share it with anybody, we can generate a Let’s Encrypt certificate to encrypt connections that reach any of the Deflect edges while connections between Deflect edges and your web server will be encrypted by your own certificate.
Enable HTTPS connections to your website under Deflect
If you are enabling HTTPS connections for the first time on your website and you don’t have a TLS certificate yet, you have 3 options.
1. Ask Deflect to do everything for you
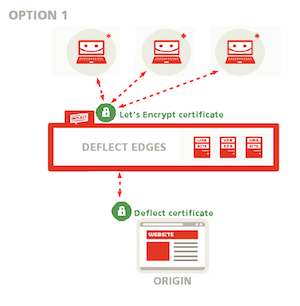
You can ask Deflect to do everything for you: we will generate a public-facing Let’s Encrypt certificate to encrypt connections between your readers and Deflect edges, and an origin certificate to secure connections between Deflect and your website (see option 1 in the public-facing certificate setup guide and option 1 in the guide to the Deflect Dashboard Control Panel). This option is recommended if you are not familiar with OpenSSL. Both public-edge and edge-origin communications will be encrypted and the edge can validate that it is talking to your server rather than some other server impersonating yours.
2. Generate your origin certificate and have it signed by Deflect
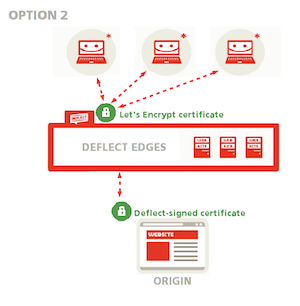
If you feel comfortable using OpenSSL, Deflect will only generate a public-facing Let’s Encrypt certificate, while you generate your origin certificate and have it signed by Deflect so that connections between edges and origin can be validated and Deflect can be sure that it is talking to your server (see option 1 in the public-facing certificate setup guide and option 2 in the guide to the Deflect Dashboard Control Panel). This is an advanced option, recommended if you are comfortable using OpenSSL and creating a certificate signing request. You won’t need to share your private key with Deflect, and the edge will still be able to validate your origin certificate.
3. Generate a self-signed origin certificate
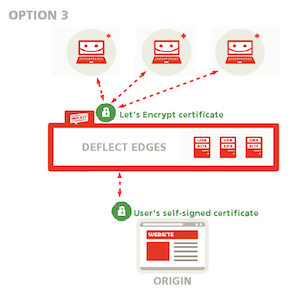
You can also generate a self-signed origin certificate without having it signed by Deflect. Deflect will only generate a public-facing Let’s Encrypt certificate, while connections between Deflect and your website will be encrypted through your own self-signed certificate (see option 1 in the the public-facing certificate setup guide). You can choose this option if you would rather not share your private key with anyone but have no experience with certificate signing requests. All connections will be encrypted, but Deflect will not be able to confirm that the certificate really belongs to you. If your website already accepts HTTPS connections and you have a TLS certificate that you would like to keep using, you have two more options:
4. Upload a custom TLS certificate bundle
In this case, both connections to Deflect and connections between Deflect and your website will be encrypted through your TLS certificate (see option 2 in the public-facing certificate setup guide). This option allows you to keep using the certificate you have already generated, but requires you to share your private key with Deflect.
5. Use a third-party certificate on your origin server
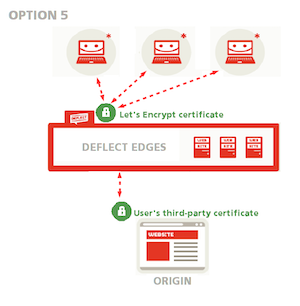
Ask Deflect to generate a public-facing Let’s Encrypt certificate while you use your third-party certificate as an origin certificate (see option 1 in the public-facing certificate setup guide). This option allows you to keep using the certificate you have already generated without having to share your private key with anyone.
Disk Encryption
Caching
Deflect practices encryption of data at rest. This means that all of our edge servers, hosting servers, logging servers and pretty much every machine that we use has either full-disk encryption or filesystem encryption for protecting the files it stores. Your web traffic cache is stored on an encrypted disk.
Logging
Your traffic logs are stored in an encrypted fashion on the Deflect edge servers and the central repository of all Deflect logs. You also have the option to switch off Deflect logging. We will then securely delete any traffic logs received on the edges, every 10 minutes. You will not get any traffic statistics in the control panel, should you wish to switch off Deflect logging.
