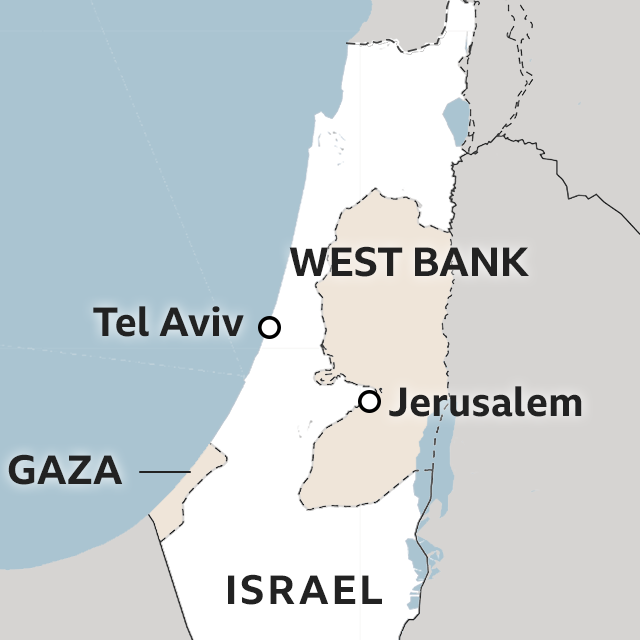
Violence that engulfed Israel and Gaza in recent weeks has permeated the digital commons as well. Since Oct 7, 2023, Deflect recorded six significant…

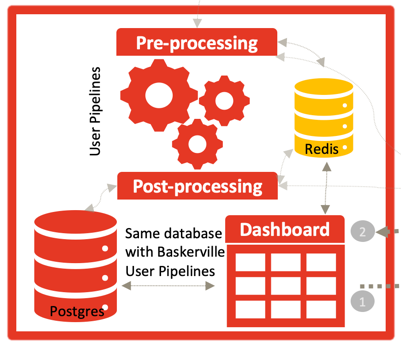
After several years of laborious effort, we are proud to announce the public release of the new Deflect software ecosystem. In our Github organization https://github.com/deflect-ca…

This was a busy month for Deflect’s mitigation tooling, with Banjax blocking almost 12 million malicious requests launched by 108,294 different bots. Due to the…

Violence that engulfed Israel and Gaza in recent weeks has permeated the digital commons as well. Since Oct 7, 2023, Deflect recorded six significant…

After several years of laborious effort, we are proud to announce the public release of the new Deflect software ecosystem. In our Github organization https://github.com/deflect-ca…

This was a busy month for Deflect’s mitigation tooling, with Banjax blocking almost 12 million malicious requests launched by 108,294 different bots. Due to the…