Normally when two computers communicate securely, without a caching proxy service like Deflect, the client (for example a browser) requests the server’s TLS certificate, checks that it trusts the certificate, then encrypts the connection using it.
ISPs, businesses and governments – those who own the networks, or any other actor sitting in the middle between the client and the server – cannot look at what’s inside the communication.
This is a good solution to prevent ill-intentioned intrusions between your readers and your website, but it clearly defeats the purpose of the distributed caching. This is because the caching proxy server, like other middle parties, does not have access to the encrypted data and is therefore unable to cache it.
To overcome this problem, Deflect has developed a system that creates two encrypted tunnels instead of just one – one for the connection between the public and the Deflect edges where your website is cached, the other for the connection between the Deflect network and your actual website (origin).
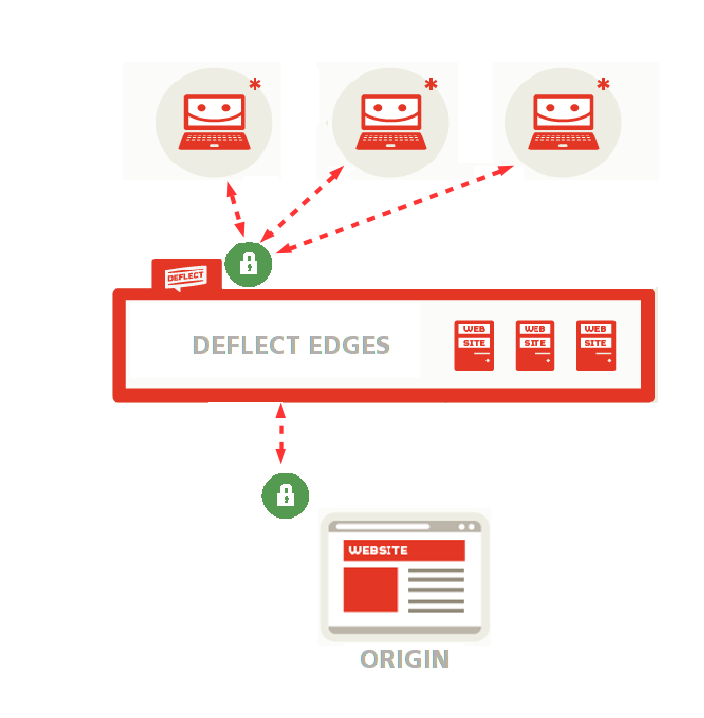
Deflect offers several options to encrypt connections to your website, and can generate TLS certificates both for encrypting connections between your readers and the Deflect edges (public-facing certificates) and between the edges and your website (origin certificates).
Deflect generates public-facing TLS certificates through Let’s Encrypt, a certification authority (CA) launched in 2015 and co-founded by the Electronic Frontier Foundation that issues free and easy-to-install SSL certificates with the explicit aim of facilitating and spreading the use of web cryptography.
Since Let’s Encrypt certificates need to be renewed frequently (every three months), to encrypt connections between edges and your web server Deflect uses longer-lasting origin certificates signed by its own certification authority.
Of course, if you already have a TLS certificate, you can use it to encrypt connections between Deflect and your website (origin certificate) as well as between the public and the edges (public-facing certificate), but in the latter case you will need to share your private TLS key with us.
If you would rather not share it with anybody, we can generate a Let’s Encrypt certificate to encrypt connections that reach any of the Deflect edges while connections between Deflect edges and your web server will be encrypted by your own certificate.
If you are not familiar with TLS but think that encrypting connections to your website is a good idea, we are willing to help! Contact us through the Deflect dashboard and we will look for a solution that can work for you.
